Now, we want to take a look at the full credentials vulnerability for an application that is implemented on the web page. So this is not a user account on a webpage that a user sets up. This is something that the server’s owner or the webpage owner sets up once using an application within a web page. Security misconfiguration includes:
Poorly configured permissions on cloud services. Default accounts with unchanged passwords. Error messages that are overly detailed and allow an attacker to find out more about the system. Having unnecessary features enabled like services, pages, accounts, or privileges.
TryHackMe (OWASP TOP 10 [Task 19])
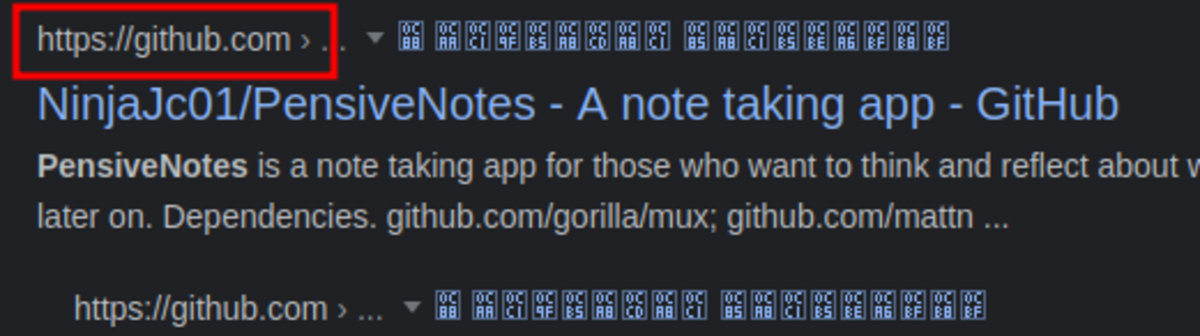
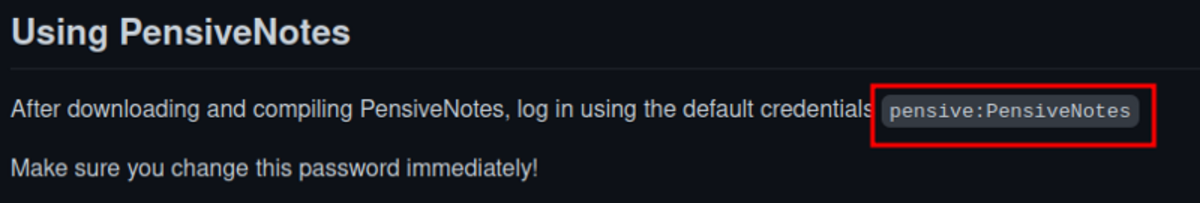
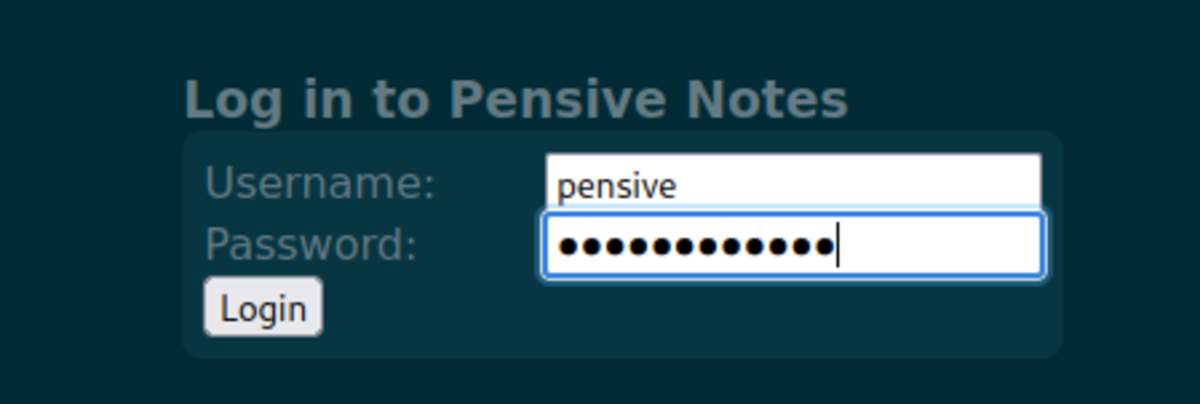
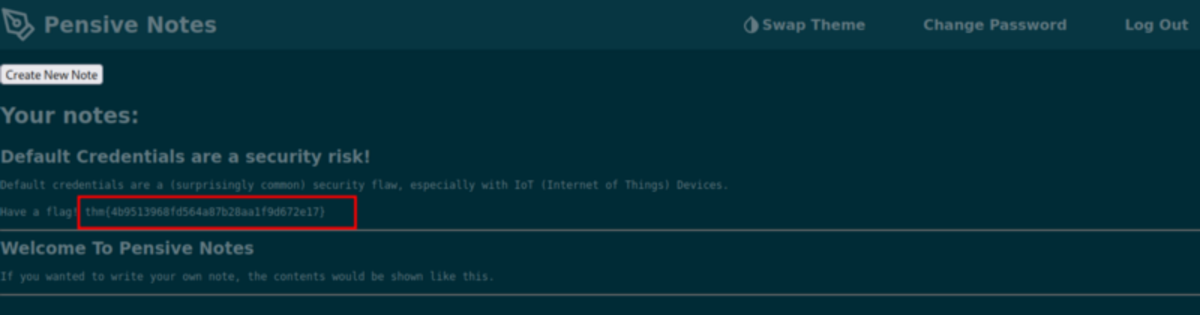
If this is your first time working on TryHackMe and you don’t know how to set it up then, check out the bonus resource section at the end. Navigate to: https://tryhackme.com/room/owasptop10 → Task 19 It says that it’s an app so let’s find it on google A GitHub repo (Hmmm…) In the README we can find the default credential to log in. Let’s try to log in with that credential. We have successfully logged in.
Resources
- 30+ Standard Linux Commands for Beginner or Intermediate Users
- Bug Bounty Hunting With Burp Suite (Intercept, Repeater & Intruder)
- Broken Access Control (Tryhackme and Owaspbwa)
- Html Injection (Tryhackme & Owaspbwa)
- Command Injection (Tryhackme & Owaspbwa)
- Website Enumeration and Information Gathering [Part 1] This article is accurate and true to the best of the author’s knowledge. Content is for informational or entertainment purposes only and does not substitute for personal counsel or professional advice in business, financial, legal, or technical matters. © 2022 Ashutosh Singh Patel